Although it has only existed as a science in recent history, forms of cryptography have been around for thousands of years. For almost as long as there's been communication, there's been some need to keep it protected until it reaches the eyes and ears of its intended audience.
But cryptography has taken on new meaning in the age of computing. The world is going digital, and keeping data safe is more important than ever. Even investors have become more aware of this important field of study in recent years. Cryptography is what puts the "crypto" in "cryptocurrency."

What is cryptography?
A simple dictionary definition of cryptography, courtesy of Merriam-Webster, is "the enciphering and deciphering of messages in secret code or cipher." Or, when it comes to computing and digital communication, "the computerized encoding and decoding of information."
When it comes to this modern era dominated by computing, cryptography has four basic goals: Information must be kept confidential, its integrity must be maintained in transit (meaning the data isn't altered), the recipient should be able to authenticate the sender, and the sender must not be able to deny sending the data or communication (non-repudiation).
How does cryptography work?
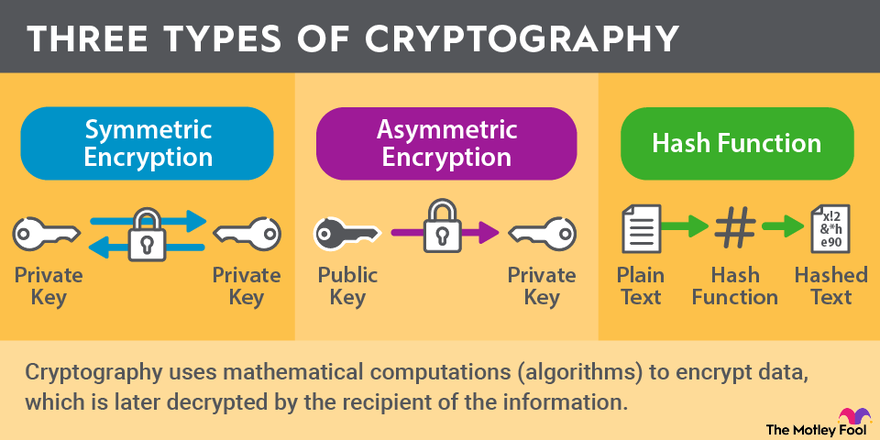
Cryptography uses mathematical computations (called algorithms) to encrypt data, which is later decrypted by the recipient of the information. To achieve the goal of data privacy, cryptography falls into three basic categories: symmetric (or single-key) encryption, asymmetric (public-key) encryption, and hash functions.
Types of cryptography
Symmetric (single-key) encryption: With symmetric encryption, data is scrambled using an algorithm. To read the information, both the sender and the receiver of data have to possess the same key to decrypt it. Symmetric cryptography is an older technology, but it's fast and efficient. The Advanced Encryption Standard (AES) was developed in the early 2000s and is one of the most commonly used forms of single-key encryption. Many branches of the U.S. government use AES.
Asymmetric (public-key) encryption: Distributing a single key for all users in a network can be difficult, which led to the more recent creation of asymmetric (or public-key) cryptography. In this system of encryption, there is a public and a private key for deciphering data. All users have both the generally distributed public key and their own private key that they might choose to share with others. Communication, such as via the internet, makes use of public-key encryption. This form of cryptography is more secure, but it's also a more taxing computation and so it's generally used for transmitting smaller amounts of data.
Hash function: Cryptographic hash functions are algorithms that make no use of keys. Instead, data is recorded into a fixed-size (usually smaller) value. This is essentially one-way encryption that creates a "fingerprint" of the information recorded, and it's done so that the contents of the new, smaller file cannot be altered.
Problems cryptography solves
In this day and age, millions of people use devices and are connected to each other. While these different users may trust each other, data and communications transferred between them may often travel along networks that cannot be trusted (such as the public internet, for example). Cryptography has become an important aspect of computing in the digital era.
More specific use cases for cryptography have emerged such as digital signature systems that help parties remotely execute contracts and agreements (e.g., the services developed by DocuSign (NASDAQ:DOCU)). Cryptography can also be used to protect information that is not in transit on a network, also called data at rest. Many types of records and databases are stored digitally now, so cryptography services are developed by cybersecurity companies to help protect organizations' critical information.
How cryptography is used in cryptocurrency
Finance is another area in which cryptography is being applied. Cryptocurrency is an example of how a network will make use of multiple encryption methods to execute, verify, and protect financial transactions.
Cryptocurrency makes use of asymmetric cryptography and hash functions. Bitcoin (CRYPTO:BTC) was the trailblazer in its use of encryption. A public key is provided for all users, along with a hash function, from which users can send and receive the digital currency. A private key is utilized to digitally "sign" a transaction to ensure the origin of a transaction is legitimate. These transactions are then recorded on Bitcoin's blockchain, a distributed ledger system that is available for anyone who wishes to use the Bitcoin network.
A hashing function is used by other blockchain networks, such as Ethereum (CRYPTO:ETH), to record information. The speed in which this mathematical puzzle is solved by a computer (or network of computers) is called the hash rate.
Pros and cons of cryptography in cryptocurrencies
Different cryptocurrencies will use different configurations of encryption methods to achieve their stated purpose, granting various levels of transaction and user anonymity. The internet has created a digital economy in which countless transactions (essentially, transmission of data from one party to another) take place every day. Cryptography is a natural fit in building a new type of digital currency, with some key attributes supporting its use:
- Cryptography helps keep information regarding a transaction secure.
- Since a blockchain is distributed to all users of a cryptocurrency, information regarding transactions is essentially tamper-proof.
- Using cryptography allows for peer-to-peer transactions without the need for an intermediary (like a bank), which reduces transaction costs.
There are some important drawbacks to the use of cryptography in digital currency:
- Cryptography is a computing function, so encrypting large amounts of data about transactions requires a lot of electricity.
- Cryptocurrency users need to use a crypto wallet to keep their digital currency secure, and losing your private security key could mean losing funds.
- Quantum computing -- which is far more powerful than more traditional computing -- is being developed for commercial use and could eventually be able to break the encryption methods used in cryptocurrencies.
As the amount of information and communication expands exponentially in the digital world, cryptography is an important underlying field of study keeping it all safe. There are lots of ways to invest in its development beyond cryptocurrencies as businesses make use of the technology to keep their various assets and day-to-day operations secure.