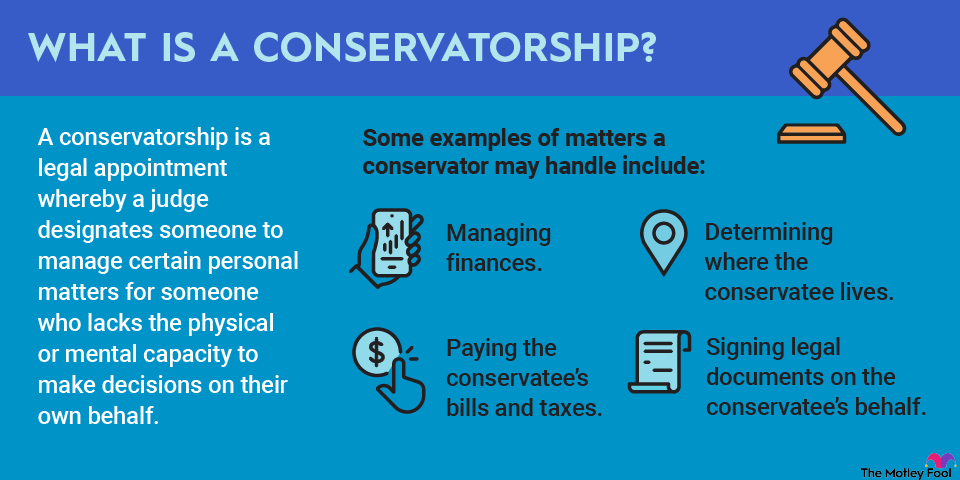
In a cryptojacking attack, the victim is tricked into running cryptocurrency-mining computer code on behalf of the attacker. It may sound harmless, but cryptojacking incidents can cause serious problems.

What is cryptojacking?
Cryptojacking is a sneaky attack. The attacker isn’t grabbing personal data or financial service logins from their victim, and the intrusion will not lock down your computer like in a ransomware attack. Instead, your computer system ends up running code that generates cryptocurrency on behalf of the intruder.
Blockchain Wallet
Cryptojacking explained
A cryptojacking attack can take many forms, but the end goal is always the same. The attacker wants to make your computer or smartphone run malicious code that generates cryptocurrency tokens without your knowledge.
The tokens are associated with cryptocurrency wallets under the intruder’s control, so the victim’s hardware essentially puts money directly into the hacker’s pocket.
The cryptojacking malware becomes a burden on the host computer, consuming resources such as memory and processor cycles. The malware may also serve as a foot in the door for more dangerous attacks, putting the victim’s private, corporate, and financial data at risk.
Crypto Tokens
How to prevent cryptojacking
Good cybersecurity practices are the best defense against cryptojacking. Here’s the drill:
- Install and run both anti-malware scanners and virus protection software where you can.
- To minimize your exposure to injection attacks, you can disable JavaScript and install ad-blocking software in your web browsers. There are downsides to this strategy since some sites won’t work properly without JavaScript and ads.
- Don’t click on emailed links unless you know that the source can be trusted -- and even then, make sure that the link points to a safe target address.
- Keep an eye on your system’s processor and memory usage and dive in for a deeper look if some process is consuming more resources than expected.
Cryptojacking hackers and security experts are always fighting to outsmart each other. The defenses that worked yesterday may be targets for a new workaround tomorrow, so it’s important to keep your anti-malware tools up to date.